Governance
Risk Management
Policy
Policy (our fundamental view)
Recognizing the various risks surrounding the NOF Group, we promote risk management initiatives with the aim of preventing the occurrence of loss risks and minimizing their impact when they do occur, thereby contributing to the achievement of management strategy targets.
- The NOF Group comprehensively identifies various management risks surrounding its business, and conducts risk assessment based on the impact and frequency of each factor in order to identify risks that need to be addressed as a priority.
- According to the characteristics of the identified risks, We work to minimize the impact on management by taking appropriate measures to reduce the impact of risks that have materialized, as well as measures to reduce the probability of occurrence.
- We work to objectively verify the effectiveness of risk countermeasures by periodically conducting risk assessments, while working to recognize and evaluate new risks.
- Under the leadership of the Risk Management Committee, we promote the risk management of the NOF Group by implementing the above risk management cycle.
Organizational Setup
The Risk Management Committee, the Compliance Committee, the RC Committee, and the Quality Control Committee analyze management risks, consider countermeasures, and report to the Board of Directors. The Board of Directors receives reports and deliberates as necessary on various business risks, including those related to compliance, information management, and environment and safety, as well as confirmation and evaluation of the comprehensiveness of risks. We manage and monitor Group companies in accordance with the rules on the management of Group companies, and offer advice, as necessary; while any important matters that are deemed to materially impact our subsidiaries’ assets or profit and loss are approved by the NOF Board of Directors or the Executive Committee.

Diagram of Risk Management Committee organization
Countermeasures
Risk assessment process
The Risk Management Committee takes the lead in preparing a list of risks in consideration of the business characteristics of each department and the environment surrounding the business, including global political, economic, and social conditions. Based on this list of risks, a questionnaire is sent to each NOF site and Group company to estimate the impact and frequency of each risk. Using the results of this questionnaire, the general managers of each division carry out risk evaluations. Based on the results, the Risk Management Committee identifies the risks whose response status should be recognized by management and consults with the Board of Directors to select the key risks for monitoring.
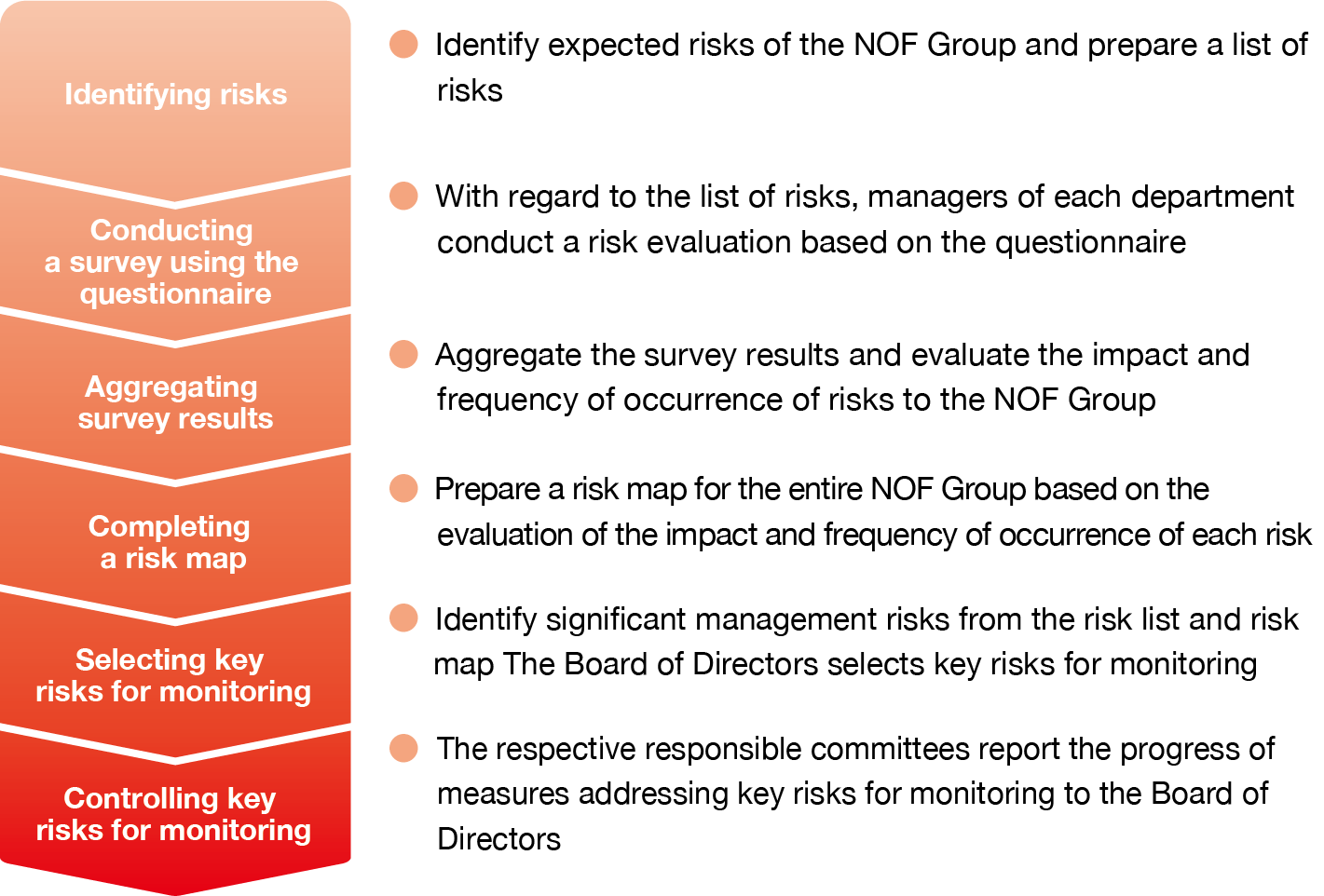
Flow of risk assessment
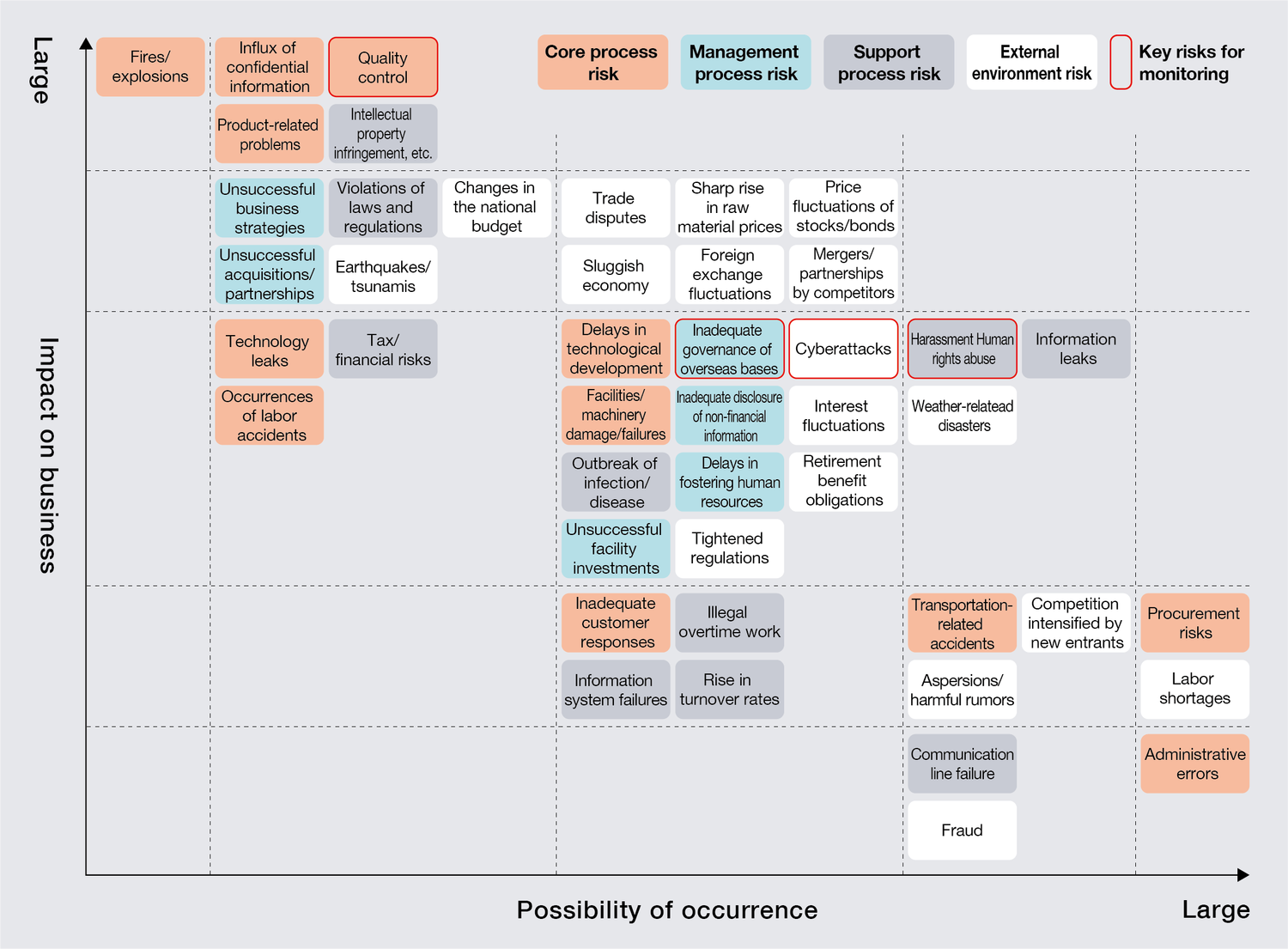
Risk map (excerpt)
The risk map is prepared based on the results of a questionnaire estimating the impact and frequency of risks at each NOF site and Group company, as well as the results of risk evaluation by managers of each department. The risk map is regularly revised and key risks for monitoring are selected in order to implement activities aimed at enhancing the NOF Group’s resilience.
Overview and status of countermeasures of key risks for monitoring
| Key risks for monitoring | Risk description | Ongoing countermeasures |
|---|---|---|
| Harassment / human rights abuses |
Possible decline in trust in the Company due to human rights abuse, such as abuse of authority and sexual harassment at workplaces |
|
| Cyberattacks and information system failures |
Possible information leaks and interruption of business activities, due to illicit access from external such as cyberattacks and information system failures |
|
| Inadequate governance of overseas bases |
Possible decline in trust in the Company due to fraud, such as violations of laws and regulations, as a result of inadequate governance at overseas bases |
|
| Quality control | Possible decline in trust in the Company due to quality fraud, falsification of quality inspection results, and other situationsRisk of a significant increase in workload due to rising customer quality demands |
|
Overview of major risks and status of countermeasures
| Major risk | Risk description | Ongoing countermeasures |
|---|---|---|
| Technology leaks | Possible decline in the NOF Group’s competitiveness, due to leakages of technology and technical information, which allows similar products/technologies to be provided by competitors |
|
| Raw material procurement | Risk of social credibility falling due to human rights violations such as forced labor and child labor, or procurement of raw materials suspected to damage the environment |
|
| Occupational accidents and incidents |
Possible casualties among employees and neighborhood residents, possible suspension of business activities, and possible compensation for damages as a result of large-scale fires and explosion accidents at plants |
|
| Intellectual property infringement, etc. |
Possible compensation for damages and possible orders to suspend manufacturing and shipment, due to infringements of intellectual property rights |
|
| Violations of laws and regulations |
Possible suspension of business activities and possible payments of surcharge, etc. following administrative dispositions taken in response to violations of laws and regulations, such as the Unfair Competition Prevention Act, Antimonopoly Act, Subcontract Act, Foreign Exchange and Foreign Trade Act, Chemical Substances Control Law, and Pharmaceutical and Medical Device Act |
|
| Earthquakes, tsunami, infectious diseases |
Possible interruption of production activities or business activities, including sales and distribution, due to earthquakes, tsunami, or other natural disasters |
|
| Delays in fostering human resources |
Possible stall in development of core human resources who will be responsible for business growth, due to a delay in implementing the human resource development plan |
|
| Inadequate disclosure of non-financial information |
Possible loss of trust from stakeholders due to uncertainty about economic and environmental impact as well as social reputation |
|
BCP Strengthening
Promotion of the Business Continuity Plan (BCP*)
NOF has formulated a BCP to enable its core business to be continued or, if damaged, to be restored quickly while minimizing the loss of business assets in the event of a natural disaster such as an earthquake or tsunami, or an emergency situation such as the COVID-19 pandemic. The activities of the BCP Subcommittee primarily focus on the formulation of a manual to determine the responses to be implemented in normal times and in emergencies, in addition to the preparation and yearly renewal of information on the estimated damages to plants and various government, infrastructure, and supply chain-related information required for resuming operations. Additionally, the BCP Subcommittee performs annual internal audits and training in an effort to firmly establish the BCP and enhance its effectiveness.
In fiscal 2024, based on the results of training from the previous fiscal year, we conducted company-wide joint training on the assumption of complex risks, including cyberattacks on overseas bases and the evacuation of Japanese employees from other countries. The training focused on smooth information sharing and cooperation between the Emergency Headquarters at the Head Office and local bases to verify the effectiveness of the BCP.
Information Security Management
Management of trade secrets and protection of personal information
NOF considers information assets such as trade secrets and personal information entrusted to us by customers or business partners, or held by us, as well as systems for utilizing such information as important management resources in corporate activities. Based on the recognition that establishing robust information security for the information assets is essential for stable management, we have established the Information Security Policy as a basic principle for promoting effective utilization and protection of information assets. At the same time, based on the recognition that protecting personal information is a fundamental social responsibility, we have established and published the Privacy Policy.
Under such policies, we have set forth specific measures for enhancing the levels of confidentiality, completeness, and availability of information and specific ways of handling personal information in our internal rules and manuals and are ensuring thorough dissemination and understanding within the company. Such internal rules and manuals include: Information Security Management Rules, Personal Information Protection Rules, Provisions Related to Information Systems, Confidential Information Handling Manual, and Information Equipment Handling Manual.
NOF Group Information Security Policy
The NOF Group considers information such as trade secrets and personal information entrusted to us by customers or business partners, or held by the Group, as well as systems, etc. for utilizing such information (below, “information assets”) as important management resources in corporate activities. Based on the recognition that establishing robust information security for information assets is essential for stable management, we have established the below Policy and ensure compliance therewith.
- The NOF Group shall develop the information security system to further strengthen the management function of information assets.
- In order to protect the information assets from leakage, falsification, and destruction, the NOF Group shall provide information security education for employees, develop regulations, and implement technical measures for information systems.
- The NOF Group shall comply with laws, regulations, codes, and contractual obligations related to information security.
- In the event of an information security incident, the NOF Group shall respond promptly and appropriately to each incident and prevent a recurrence.
- The NOF Group shall maintain and continually improve these efforts in this Policy.
Management system
In the internal organizational aspect, the Information Security Management Subcommittee is set up to deliberate and make decisions on important matters related to information security. Under the Information Security Management Supervisor, who is the chairperson of the Subcommittee, document information security management supervisors, electronic information and information system security management supervisors, personal information complaints handling supervisors, as well as a person responsible for management at each division, site, and department are appointed to manage the implementation of specific measures. Against threats such as unauthorized access from external, information leakage, falsification, and destruction, appropriate and reasonable security measures are implemented. In addition, NOF continually reviews and strives to improve the information security management and personal information protection systems and measures through internal audits.
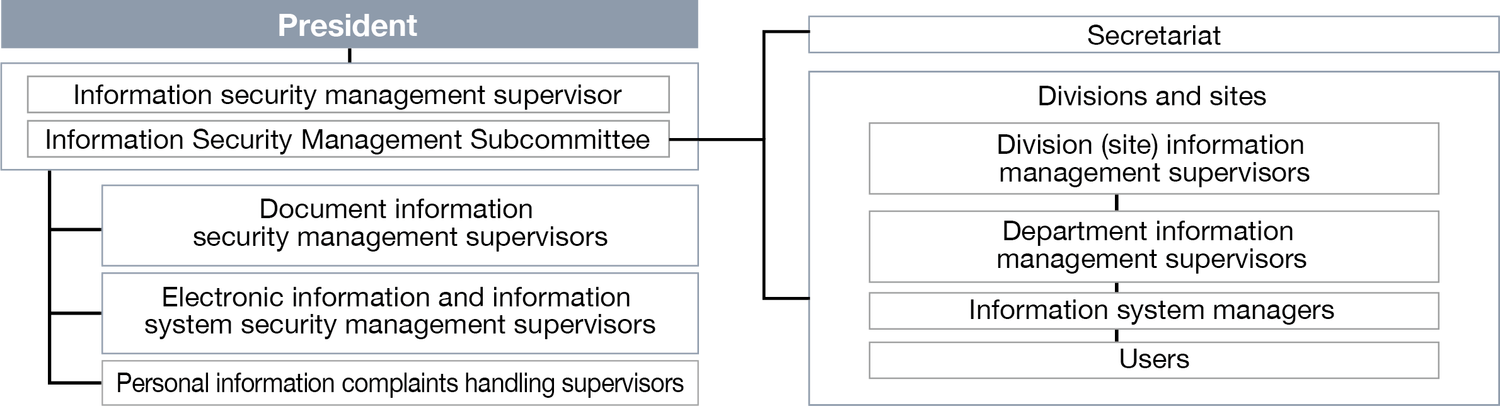
Diagram of NOF’s information security management system
Risks and opportunities in information security and measures against risks
| Risks and opportunities | Details | Measures |
|---|---|---|
| Risks |
|
|
| Opportunities |
|
- |



